This article is being updated. Please be aware the content herein, not limited to version numbers and slight syntax changes, may not match the output from the most recent versions of Bright. This notation will be removed when the content has been updated
What is PWM?
PWM is an open source self-service password application for LDAP directories. PWM is an ideal candidate for organizations that wish to “roll their own” self-service password solution, but do not wish to start from scratch.
It can be installed as follows:
Install Tomcat on top of a Bright Cluster
- Install tomcat from the base distribution repository:
[root@ma-b72-c7 ~]# yum install tomcat
- Add the following JAVA_OPTS line to /etc/tomcat/tomcat.conf configuration file. Feel free to change the Xmx and MaxPermSize values, these settings affect how much memory tomcat will use:
JAVA_OPTS="-Djava.security.egd=file:/dev/./urandom -Djava.awt.headless=true -Xmx512m -XX:MaxPermSize=256m -XX:+UseConcMarkSweepGC"
- The following line should be added for PWM version 1.8 to work with tomcat:
PWM_APPLICATIONPATH="/var/lib/tomcat/webapps/pwm/WEB-INF"
- Install the admin packages:
[root@ma-b72-c7 ~]# yum install tomcat-webapps tomcat-admin-webapps
- Configure tomcat to use port 9085 instead of the default port:
[root@ma-b72-c7 ~]# grep 9085 /etc/tomcat/server.xml
<Connector port="9085" protocol="HTTP/1.1"
[root@ma-b72-c7 ~]#- Add an admin user and password to access the web interface:
[root@ma-b72-c7 ~]# grep -r user /usr/share/tomcat/conf/tomcat-users.xml
<tomcat-users>
<user username="admin" password="system" roles="manager-gui,admin-gui"/>
[...]
</tomcat-users>- Enable/Start the tomcat service
[root@ma-b72-c7 ~]# systemctl enable tomcat
[root@ma-b72-c7 ~]# systemctl start tomcat
- Add a shorewall rule to allow access to port 9085:
[root@ma-b72-c7 ~]# grep 9085 /etc/shorewall/rules
ACCEPT net fw tcp 9085
[root@ma-b72-c7 ~]# service shorewall restart
Install PWM
- Download the sources for PWM 1.7.1
https://drive.google.com/folderview?id=0B3oHdiTrftrGV3ZrMi1LUzVCY1U&usp=sharing#list
- Unzip the sources:
[root@ma-b72-c7 ~]# mkdir pwm-1.7.1
[root@ma-b72-c7 ~]# mv pwm_v1.7.1.zip pwm-1.7.1
[root@ma-b72-c7 ~]# cd pwm-1.7.1
[root@ma-b72-c7 ~]# unzip pwm_v1.7.1.zip
- Copy the pwm.war file to tomcat webapps:
[root@ma-b72-c7 ~]# cp pwm-1.7.1/pwm.war /var/lib/tomcat/webapps/
- Restart tomcat and check if the pwm is accessible
[root@ma-b72-c7 ~]# systemctl restart tomcat
Access at:
http://your-machine.com:9085/pwm/
- The first time the PWM web interface is accessed, it will offer a configuration guide to help in doing the initial configuration:

- Click on “Start Configuration Guide” to start the guided configurations.
- Choose the backend LDAP server and click “Next”

- Add port 389 to the list of allowed ports in shorewall:
[root@ma-b72-c7 ~]# grep 389 /etc/shorewall/rules
ACCEPT net fw tcp 389
[root@ma-b72-c7 ~]# systemctl restart shorewall
- Enter the LDAP configuration in the web form:

- Define an admin user:
[root@ma-b72-c7 ~]# cat adminuser.ldif
# adel, cm.cluster
dn: uid=adel,dc=cm,dc=cluster
uid: adel
objectClass: inetOrgPerson
objectClass: posixAccount
objectClass: shadowAccount
loginShell: /bin/bash
uidNumber: 1001
gidNumber: 1002
cn: adel
homeDirectory: /home/adel
shadowMin: 0
shadowMax: 999999
shadowWarning: 7
shadowInactive: 0
shadowExpire: 24837
shadowLastChange: 16792
sn: adel
mail:
memberof: cn=admins,ou=Group,dc=cm,dc=cluster
[root@ma-b72-c7 ~]# ldapadd -x -W -D "cn=root,dc=cm,dc=cluster" -f adminuser.ldif
Enter LDAP Password:
adding new entry “uid=adel,dc=cm,dc=cluster”
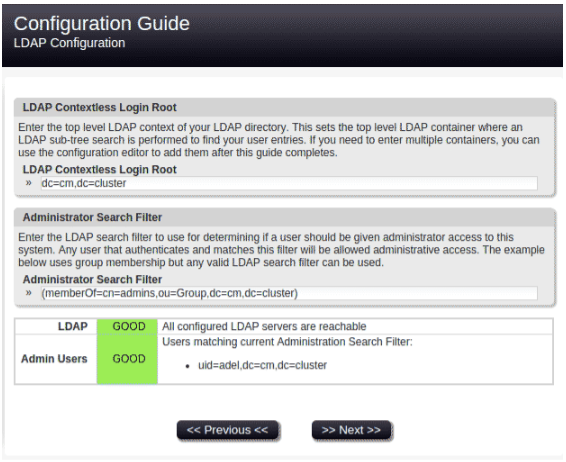
- Add a test user:

- Enter a configuration password. This allows the global configurations for PWM to be set:

- Complete the configuration by saving it

- Create a PWM schema file:
[root@ma-b71-c7 ~]# cat /cm/local/apps/openldap/etc/schema/pwmschema.schema
attributetypes ( 1.3.6.1.4.1.35015.1.2.1
NAME 'pwmEventLog'
SYNTAX 1.3.6.1.4.1.1466.115.121.1.40
X-ORIGIN 'user defined' )
attributetypes ( 1.3.6.1.4.1.35015.1.2.2
NAME 'pwmResponseSet'
SYNTAX 1.3.6.1.4.1.1466.115.121.1.40
X-ORIGIN 'user defined' )
attributetypes ( 1.3.6.1.4.1.35015.1.2.3
NAME 'pwmLastPwdUpdate'
SYNTAX 1.3.6.1.4.1.1466.115.121.1.24
SINGLE-VALUE
X-ORIGIN 'user defined' )
attributetypes ( 1.3.6.1.4.1.35015.1.2.4
NAME 'pwmGUID'
SYNTAX 1.3.6.1.4.1.1466.115.121.1.7
SINGLE-VALUE
X-ORIGIN 'user defined' )
objectclass ( 1.3.6.1.4.1.35015.1.1.1
NAME 'pwmUser'
DESC ''
SUP top AUXILIARY
MAY ( pwmEventLog $ pwmGUID $ pwmLastPwdUpdate $ pwmResponseSet )
X-ORIGIN 'user defined' )
[root@ma-b71-c7 ~]#- Include the PWM schema with an include statement in slapd.conf:
[root@ma-b72-c7 ~]# grep pwm /cm/local/apps/openldap/etc/slapd.conf
include /cm/local/apps/openldap/etc/schema/pwmschema.schema- Add the following write access attributes to slapd.conf
[root@ma-b72-c7 ~]# cat /cm/local/apps/openldap/etc/slapd.conf
[...]
access to attrs=pwmUser
by * read
by * write
access to attrs=pwmResponseSet
by * read
by * write
access to attrs=pwmEventLog
by * read
by * write
[...]
[root@ma-b72-c7 ~]# systemctl restart slapd.service
Configuring Password Policy and Challenge Policy
- Once you log in PWM, click on Configuration Manager, which is at the very top of the screen in the yellow bar:
- In the configuration manager click on the “Configuration Editor” button:

- You’ll be asked for the Configuration Password which was set during the initial configurations:

- Disable forcing challenge policy:


- Save changes

- Change Password Policy

- After clicking on “Password Policy” you’ll be redirected to the where you can enforce different attributes for a password. Edit as required and then save changes by clicking on “Actions” → “Save”

- When a user attempts to modify a password using the PWM web interface, the password policy is followed:

- A user can only change the password when the password matches all the enforced password policy rules:

References
https://github.com/pwm-project/pwm
Troubleshooting
- Check the admin user exists
[root@ma-b71-c7 ~]# ldapsearch -x -b dc=cm,dc=cluster memberOf
# extended LDIF
#
# LDAPv3
# base <dc=cm,dc=cluster> with scope subtree
# filter: (objectclass=*)
# requesting: memberOf
#
[...]
# adel, cm.cluster
dn: uid=adel,dc=cm,dc=cluster
memberOf: cn=admins,ou=Group,dc=cm,dc=cluster
# search result
search: 2
result: 0 Success
# numResponses: 10
# numEntries: 9
