By default, Cluster Extension (hybrid) cloudbursting uses UDP port 1194 to run a VPN tunnel between the head node and the cloud.
The port and protocol used can be changed with a AdvancedConfig directive in /cm/local/apps/cmd/etc/cmd.conf. The cmd.conf file and its standard directives are described in Appendix C of the admin manual.
An aside about the AdvancedConfig directive:
AdvancedConfig values are not part of the standard directives and might not be documented for use by the Bright Cluster Manager administrator. AdvancedConfig directive values are added by appending them to any existing AdvancedConfig key/value pairs. There can be only one AdvancedConfig line, containing various configuration directives. For example:
AdvancedConfig = { "param1=value1", "SlurmDisableFastSchedule=1", "param2=value2" }
For VPN, port and protocol can be configured. For example, the AdvancedConfig line for port 443, using the TCP protocol: AdvancedConfig = {"CloudVpnPorts=443", "CloudVpnProtocol=tcp"}
Default values used by cmd, are not set in AdvancedConfig. Because of that, the default VPN protocol/port is not found there. Specifying them is only necessary if the defaults are changed.
After modifying the AdvancedConfig line, the cloud node and cloud director instances must be terminated. Powering them off and on is not enough.
To terminate an instance, the “terminate” command is used in the “cloudsettings” mode of the node object, as seen below:cloud-sles:/home # cmsh[cloud-sles]%[cloud-sles]% device cloudsettings us-east-1-director[cloud-sles->device[us-east-1-director]->cloudsettings]% terminate
cmd service must be restarted on the head node to reload the cmd.conf file:
systemctl restart cmd.service
After the cmd service is restarted, before powering on the directors and the cloud nodes again, new ports need to be added to the security group attached to the cloud director. By default, it’s a security group with a name starting with “director-sg”. This security group will have a “Custom UDP” rule that specifies port 1194. The rule can be edited to allow a new port that was specified in cmd.conf. For example, if the configuration was changed to TCP/443, the corresponding security group will be changed as:
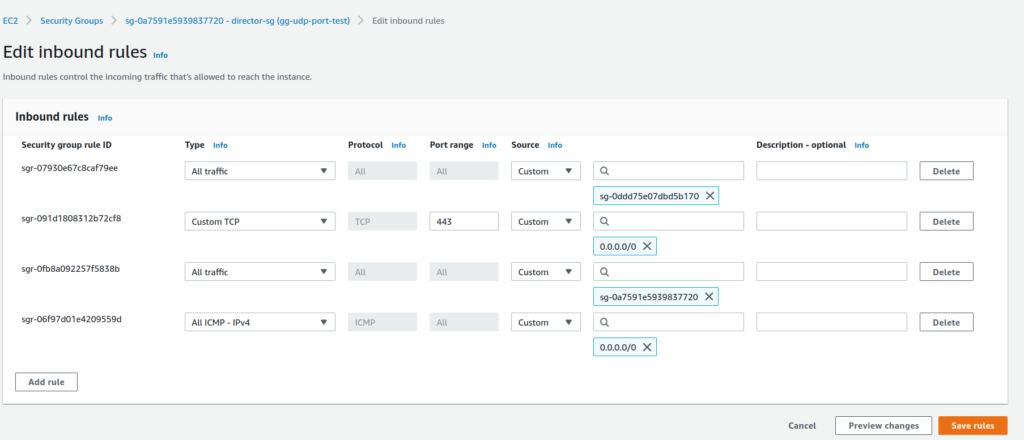
The cloud instances that are started up from now on will use the new port and protocol.
To verify the changes are present on the cloud director, the “nextinstallmode” property of the cloud director node object can be set to “main”. This makes the cloud director halt in the node-installer phase the next time it starts. The administrator can access the cloud director over ssh and examine the following file:
cat /etc/openvpn/vpn.0.conf
This is the OpenVPN configuration file on the cloud director. If all is good, the cloud director can have a ‘power reset’ carried out on it.
The ports and the protocol used by OpenVPN can be found in the/etc/openvpn/client-tunX.conf
files on the headnode. There is one file for each amazon region defined by the admin The file gets created/updated after the cloud director is started.
An example line in the file might be:
remote 54.237.150.12 443 tcp
which means:
remote <cloud-director-ip> <remote-port> <protocol>
The port and protocol here correspond to the AdvancedConfig directives for "CloudVpnPorts=443", "CloudVpnProtocol=tcp"
